|
|
 |
Read Chapter 14 in your text and this lesson. Then, complete hw14. This lesson introduces the Internet Protocol, or IP. IP provides a global addressing scheme that permits packets from any host on the Internet to reach your end station, and vice versa. In Lessons 15 and 17, we'll concentrate on how IP works, how it is used to move packets through internetworks, and how TCP is used at layer four to ensure all the datagrams of a transmission are accounted for. Internetworking at Layer 3 As you may remember, the Network layer is responsible for end to end addressing and pathway determination through the network for connectionless services. IP provides the rules for creating a datagram header that permits a datagram to be routed through a complex maze of interconnecting networks. IP addresses are logical addresses. They are independent of local area network architecture and there is a single range of addresses used for anyone wishing to interconnect with the Internet. By requesting a small portion of the address space, you may add your own network end stations to a LAN and attach your LAN, through a router to a network that is already a part of the Internet. Once you interconnect to your "upstream provider", an ISP, you'll have access to the Internet. Global management of the address space is required because IP addresses must be unique. The IP address assigned to your end station must not be a duplicate of any other IP address because routers have to send packets Internet Protocol is not the only addressing scheme that will allow internetworking. AppleTalk, IPX (Novell), Banyan Vines, Apollo, and other protocols allow end stations on various networks to communicate through routers. Multiprotocol routers can pass layer three packets of more than one protocol type simultaneously. That means you can have AppleTalk, IPX and IP running on your internetwork all at the same time. Both Cisco and Cabletron make multiprotocol routers. Routed protocols are those that handle addressing of end stations for internetwork communication. Routing protocols (not the same thing) use algorithms and specific procedures to update and maintain routing tables.
<shameless_plug> If you are interested in investigating other routed protocols, sign up for Datacom 2 next semester. For example, you can devise your own experiments with Novell or AppleTalk on the experimental network in our lab. </shameless_plug> IP resides at layer three of our Internet Model. Above IP, at layer four, resides TCP, UDP and many other protocols. Take a look at this graphic, similar to the one in your book and the one in the on-line RFC.
Protocols at layer five of the Internet model are supported by layer protocols such as TCP and UDP which we will discuss in Lesson 17. At layer three, the Internet Protocol supports the "routability" of all data segments created by these upper protocols. The above graphic is a derivative of one that was first published as RFC 791 in September 1981. Many of the concepts covered here are also covered in RFC 791. Another function of IP is to break up data that is too large to be transmitted in a single frame at layer two. This is called segmentation or fragmentation. Each fragment gets an IP header which has to have identifying information added to it so that the original datagram can be reconstructed when all the fragments arrive at the destination. The fragments are valid layer three datagrams in their own right. For example, an FDDI connection will allow frames that are about 4500 bytes long, but Ethernet only permits frames of about 1500 bytes. Frames received at a router on an FDDI link will be fragmented before they are sent out on the Ethernet link. Please remember the following important features of IP:
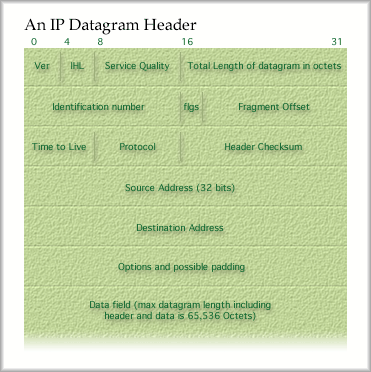
Through revision and additions, the Internet standard has reached version 4, which is the base for nearly all IP implementations at this time. Because we are running out of IP addresses however, there is work progressing on IPv6. Few organizations have moved to IPv6 at this time, but the need for additional address space may drive this migration. Stay tuned to your local Internet news to keep track of these developments or <shameless_plug> bring the topic up in Datacom 2 next semester. </shameless_plug> The IPv4 packet
Let's walk through the fields as they are listed here. * Ver, or version, is four bits that must come first. They define the version of IP. When an IPv6 packet comes in, it has four bits for version as well. After that the version six packet is different. The router inspects the first four bits to determine what version of it is looking at and then proceeds to process the fields that follow * IHL stands for Internet Header Length. It is the length of this IP datagram header counted in 32-bit words. The header shown above has six so the field would hold 0110. * The Service Quality field was an attempt to provide different service qualities, like priority of the datagram, what kind of delay it can accept and so on. The implementation of this field has not had the desired effects of offering quality of service. It is not a true quality of service and IP is not reliable anyway. Not much benefit has been realized through the use of these bits. * The Total Length field holds the length of the datagram in octets. This field has 16 bits so the maximum length of a datagram, including data and header fields, is 65,536 octets. * Identification Number is a value that is used to help reassemble the pieces of a fragmented datagram. * Flgs is my shorthand for Flag Bits. The first of these three bits is reserved and must be zero. The next bit, the Don't Fragment bit indicates that this datagram must not be fragmented if it is set to one (unless a system can perform transparent fragmentation). The third bit is called the More bit. It functions just like the More bit in an X.25 Packet Layer packet. A 1 indicates more fragments are to come and a 0 indicates this is the last fragment. * The Fragment Offset field shows what part of the original datagram this came from. This is another part of the puzzle used to reconstruct the pieces of the original datagram. * Time to Live contains a self-destruct countdown timer for the packet. Each time a datagram enters a router, this value is decremented. If the value reaches zero, the router will discard the packet immediately. * The Protocol field has a value that tells the end station what service at layer four should handle this datagram, TCP or UDP for example. This feature is important because it permits you to have multiple layer four connections open at once, all running through one implementation of IP on your computer. * The Header Checksum determines if an error occurred in the header. If an error is found, the datagram is discarded. No notification is sent to anyone that the datagram met an untimely death. * A 32-bit Source Address and Destination Address simply indicate the IP address of the origin and destination for this datagram. We'll discuss IP addresses a bit later. * Finally, an Options and Padding field is included. The options field is not required, but permits some additional features. The padding makes sure that the header ends on a 32-bit word boundary. Padding is always set to zero. An IP datagram must be at least 21 octets long. That would be five 32-bit words for the required fields in the header and one octet for the data field. The maximum size of an IP datagram is 65,536 octets, inclusive of header and data. 32-bit IP Addresses
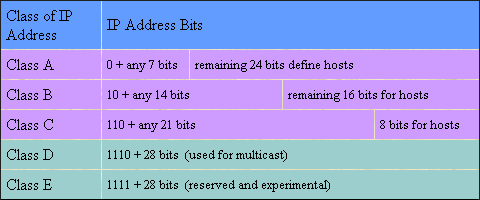
Class A, B and C addresses are distributed to organizations. A fixed network address is given and the organization can assign the host region as is desires. For Example, Stanford University has 00100100 as the first 8 bits in its Class A address. The remaining 24 bits are free to be assigned as necessary to hosts at Stanford University. Whoa, that gives Stanford 16,777,216 host addresses. Note that the first 8 bits are fixed when an organization receives a Class A address and that Any address that starts with a zero is a Class A. The first 16 are fixed when a Class B address is assigned, such as the first 16 bits in the Class B address of the University of Colorado, 10000000 10001010. Class B addresses always start with a one-zero. Fort Hays has over a dozen Class C addresses. The first 24 bits of a Class C address are fixed when assigned to an organization. The first three bits of all Class C addresses are one-one-zero. For example the Advanced Technologies Lab has addresses in the following range:
Note that the first 24 bits are fixed and the host range, the last eight bits are free to the ATL to assign. Actually some of these are used by other locations on campus so we don't get all 255 addresses in this range. Hey, aren't those bits difficult to read and remember? Woudn't it really be a drag to type those in to a web browser every time you wanted to check your mail on Hotmail or Yahoo? For our own comfort we've created a scheme to represent the bits of an address in base 10, called dotted decimal format. The bits are divided into groups of 8 and then each group is converted to base 10. The number will range from 0 to 255. The four numbers are arranged side by side and decimal points (called dots, of course) are used to separate them. The ATL has a machine with the following address: 11000110 11111000 01100110 00101010 Or, 198.248.102.42 OK, so now you get your chance to practice all that base-2--base-10 conversion stuff we did way back at the beginning of the semester. So how do routers actually decide which direction to send a datagram? The answer is they look for the address in the datagram header, consult a table that matches the address with an outgoing line and then they put that datagram in the outgoing queue for that line. There is a problem with this, though. The router would have to have every possible address in its table and that would amount to over 4 billion address entries with 4 billion matching outgoing lines. Hmm, that's too much. We'd need about 9 Gigs of RAM in the router to hold that table. Obviously, that's not a workable solution. There are a few things we can do to limit the table size. Create a scheme that allows us to keep an entry for a network address and then just forward all hosts to the outgoing line that matches that single entry in the routers table. We can establish default routes for datagrams destined for addresses we don't know how to route. These two techniques are used extensively as it turns out. Using a major network mask, a router can extract the major network number from a unique IP address. Then, the router only needs to keep one address for all the hosts on a particular network. A mask uses a binary AND function (basically like multiplication) to calculate the network address that a destination address belongs to. Binary AND: 1 AND 1 is 1 0 AND anything is 0 Destination Address Mask bits, use a 1 to The network Routers also use default routes to forward packets that they don't have entries for. This keeps routing tables very small. The hope is that someone upstream will be able to route the packet eventually. OK, so you don't like having to remember all that dotted decimal stuff either. When you type in an address to your web browser, why isn't it a number, right? Numbers are too hard to remember for normal people. Only your propeller spinning professor enjoys them. For the rest of the planet the DNS system was devised. DNS stands for Domain Name System. Simply, this is a computer server that holds a table of nicknames, in what I like to call dotted-English, that are matched to the address. You type in something like mail.excite.com and your browser makes a request of to the DNS server for the actual address (binary). After the actual address is obtained, the browser can request the page from Excite. DNS servers constantly communicate with each other to keep their databases up to date. Even so, when a DNS server doesn't have an entry for your request, it can send your request up stream to a "smarter" DNS server. If your request reaches the top level domain and no entry is found, you'll get the dreaded "You're goin' nowhere, baby!" message in your browser.
Coming soon, in Lesson 17, we'll discuss the TCP and UDP, two "Host-toHost" communications protocols that operate at Layer 4 of the OSI model and that rely on IP for internetwork addressing and segmentation. |
| [INF 680 Syllabus] [How to Start] [Schedule] |
Used with permission of the Author; Copyright (C) Kevin A. Shaffer 1998 - 2018, all rights reserved. |